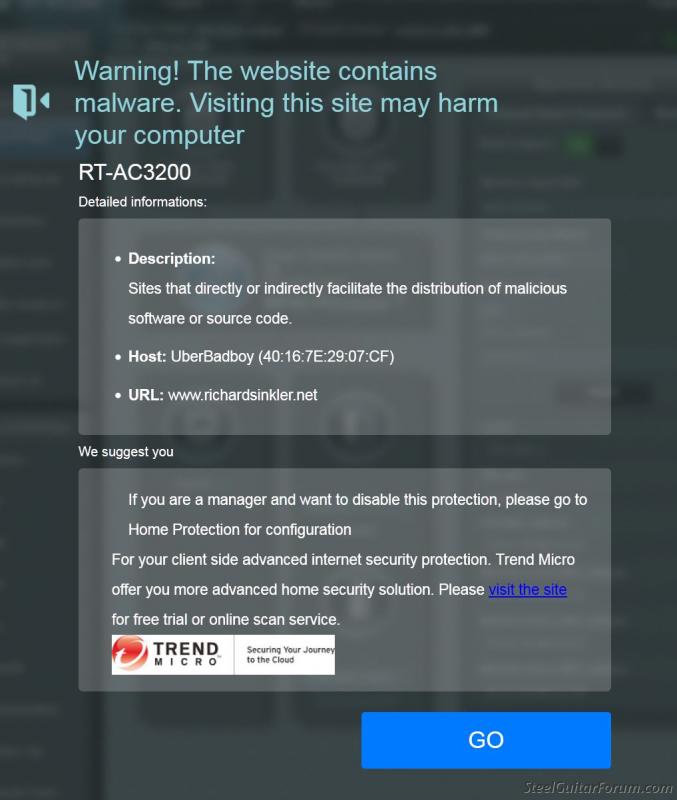
Richard Sinkler wrote:Thanks. I plan on emailing their tech support today with the info above with the screen shots. It's definitely strange. In the meantime, I have removed any links to my site from the forum as a precaution, until I figure it out. I may just end up pulling my site down altogether.
Why do that? You have a static website, based upon html 5, CSS3 and JavaScript. The only ways that your pages can be infected/compromised are:
- A keylogger on your computer that watches for you to log into an ftp location or cpanel website;
- Socially Engineering your login credentials from you through trickery;
- A rogue employee/partner/Webmaster with your login credentials;
- The innocent use of a 3rd party script, cms, cart or active app that has a XXS flaw known to hackers;
- Malvertising exploits on an ad platform targeting visitors running outdated plug-ins (and 0-day exploits);
- Server compromise you have no control over.
Most of these vulnerabilities are within your control. If you don't have 3rd party ads on your pages, that is removed from the equation. Note that these attacks target your visitors browsers, not your actual web pages. They are few and far between. Those that exist only run against certain browsers and are short lived before being taken down by the ad network.
Vulnerabilities in 3rd party apps, like WordPress, Joomla, Magento, Zen Cart and the like, are usually discovered/reported to the maintainers who release patched versions very quickly. Most of these active apps that are available through 3rd party scripts are automatically updated as problems are discovered.
The last item, server compromise, is outside your control. It's not your server. If you should ever discover that your web host has allowed your shared hosting account to be compromised via a root attack on their server, move to another host who is better protected against these attacks.
Finally, you can sign up with any of the various safety scanning services to check your pages for malware. Securi and Sitelock are two that comes to mind. There are free and paid scanning options. Free is usually good enough for static sites like yours. I use Sitelock, which is offered for free by
my web host, Bluehost. They also take care of updating vulnerable scripts that are available to their customers through cPanel.
Most common website compromises happen when the webmaster installs a script that is later discovered to be exploitable, but fails to update it as soon as the patched version is released. Smart webmasters use automatic updates and update notifications from script vendors.